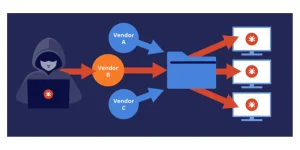
Imagine a world where a single, seemingly insignificant breach can cripple not just one company, but an entire network of businesses. This is the chilling reality of supply chain attacks, a rapidly evolving threat landscape that exploits the interconnected nature of modern business. If you’re interested in a rewarding career safeguarding businesses and individuals from digital threats, consider enrolling in a comprehensive Cyber Security Course in Bangalore.
In simpler terms, these attacks target a company’s vendors, suppliers, or partners to gain access to the main organization’s systems. Think of it like a burglar targeting the back door of a house instead of the front – unexpected and potentially devastating.
Why Supply Chains Are Vulnerable
The rise of supply chains can be attributed to globalization and the need for efficiency. However, this interconnectedness creates a web of dependencies, where a weakness in one link can compromise the entire chain. Here’s why supply chains are particularly vulnerable:
- Varied Security Standards: Companies often work with a diverse range of vendors, each with their own security protocols. This lack of uniformity can create a weak link in the chain that attackers can exploit.
- Limited Visibility: Organizations may not have complete visibility into the security practices of their vendors. This lack of transparency makes it difficult to identify and address potential vulnerabilities.
- Data Sharing: Supply chain relationships often involve the sharing of sensitive data, like customer information or intellectual property. A breach at a vendor can expose this data, leading to significant consequences.
How Supply Chain Attacks Work
The tactics employed in supply chain attacks can be quite sophisticated, but here are some common methods:
- Malware Injection: Attackers introduce malicious code into software updates or tools used by the vendor. This malware can then be passed on to the main organization, infecting their systems. Cyber Security Course in Marathahalli equip you with the knowledge and skills necessary to identify, prevent, and mitigate cyberattacks, making you a valuable asset in today’s digital world.
- Man-in-the-Middle Attacks: Attackers intercept communication between the vendor and the main company, potentially stealing data or injecting malicious code.
- Watering Hole Attacks: Attackers compromise a website or service frequently used by vendors. When a vendor employee visits the compromised site, their device can be infected with malware.
- Phishing and Social Engineering: Attackers target vendor employees with emails or phone calls, tricking them into revealing sensitive information or granting access to systems.
Real-World Examples: A Grim Reminder
Supply chain attacks are not hypothetical threats; they have very real consequences. Here are some high-profile examples:
- SolarWinds Supply Chain Attack (2020): This attack compromised a software update from SolarWinds, a company that provides IT management software. The attack ultimately affected thousands of organizations around the world.
- Target Breach (2013): Hackers infiltrated Target’s system through a compromised HVAC vendor, ultimately stealing the credit card information of millions of customers.
Protecting Yourself from the Supply Chain Threat
While supply chain attacks present a significant challenge, there are steps organizations can take to mitigate the risks:
- Vendor Risk Management: Conduct thorough assessments of potential vendors’ security practices before entering into partnerships.
- Contractual Security Clauses: Include security clauses in contracts with vendors, outlining specific security requirements and breach notification protocols.
- Data Sharing Minimization: Limit the amount of sensitive data shared with vendors and implement access controls to restrict who can access this data.
- Security Awareness Training: Train employees on the risks of supply chain attacks and how to identify and report suspicious activity.
- Continuous Monitoring: Monitor your systems for anomalies and suspicious activity that might indicate a breach has occurred.
The Future of Supply Chain Security
Supply chain attacks are a wake-up call for businesses. As the threat landscape continues to evolve, collaboration and information sharing between all players in the supply chain will be crucial. Additionally, embracing new technologies like blockchain, which can provide greater transparency and traceability, can potentially strengthen the security posture of interconnected systems.
By taking proactive measures and fostering a culture of security awareness, organizations can build more resilient supply chains and safeguard themselves from the ever-present threat of infiltration. Remember, in the age of interconnectedness, security is not just about protecting your own systems – it’s about fortifying the entire ecosystem you operate within. Training Institute in Bangalore equip you with the knowledge and skills necessary to identify, prevent, and mitigate cyberattacks, making you a valuable asset in today’s digital world.
Also Check: Cyber Security Interview Questions and Answers